If you enabled file and printer sharing in Windows you can access shared folders from a remote machine. By Windows shares administrative folders like IPC$, Admin$, C$ (and all other disks) for administrative purposes.
 Since Windows XP you need to enable access to these folders if you want to access them with a local account (like Administrator). Domain accounts with administrative permissions on the system are always allowed to access the administrative shares.
Since Windows XP you need to enable access to these folders if you want to access them with a local account (like Administrator). Domain accounts with administrative permissions on the system are always allowed to access the administrative shares.
Windows XP
When you access a non-domain joined Windows XP machine all local accounts authenticated via a network logons are treated as the Guest account. This means that even when you authenticate with an administrative account, access to the administrative share is denied.
The security policy “Network access: Sharing and security model for local accounts” (found in Computer Configuration\Windows Settings\Security Settings\Local Policies\Security Options) has two models:
- Classic: Local users authenticate as themselves.
- Guest only: Local users authenticate as Guest.
By setting the policy to Classic (pre Windows XP) you’re able to access the administrative share. 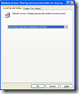
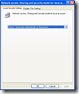
Registry key
Key: HKLM\SYSTEM\CurrentControlSet\Control\Lsa\forceguest Type: DWORD (32-bit) Value Value: 0 – Classic 1 – Guest only
Symptoms
When you try to access the network computer with a local account with administrative permissions, you receive an error message that resembles the following:
xxxxxxx is not accessible. You might not have permission to use this network resource. Contact the administrator of this server to find out if you have permissions. Logon failure: unknown user name or bad password
Windows Vista / Windows 7 / Windows 8
In Windows Vista / Windows 7 / Windows 8 a similar technique is used to prevent remote access with a local account. Instead of authenticating users as Guest (as with Windows XP) the User Account Control (UAC) remote restriction filters the administrive groups from the token, preventing the user from accessing the administrative shares.
Disabling the UAC remote restrictions is done with a registry key. After applying the remote registry I found it necessary to reboot the machine (although some articles tell differently).
Key: HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system\LocalAccountTokenFilterPolicy Type: DWORD (32-bit) Value Value: 0 - build filtered token (Remote UAC enabled) 1 - build evelated token (Remote UAC disabled)
Symptoms
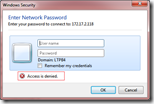 When you try to access the network computer with a local account with administrative permissions, you receive a dialog that resembles the following:
When you try to access the network computer with a local account with administrative permissions, you receive a dialog that resembles the following:
Enter Network Password Enter your password to connect to: xxx.xxx.xxx.xxx (x) Access is denied
Thank you for always sharing this useful tips and information</a